Table of contents
- Is WordPress safe?
- Does WordPress have security gaps? And if so, what can be done about it?
- 12 tips on what to consider when securing WordPress sites
- 4 Tools to check WordPress security
- 7 Plugins to Improve WordPress Security
- Conclusion: WordPress can be easily secured with simple measures
If the website is one of the most important resources for your business, the fear naturally arises quickly that it will be hacked and thus gone.
In fact, you can protect yourself quite simply from this, or at least reduce the likelihood that an attack will be successful. With some measures, you can make your WordPress installation more secure, most of which are once-off things to implement.
Let's get started and not only make your website more secure, but at the same time also get a better understanding of where the attack points lie.
Is WordPress safe?
Over 43% of all websites worldwide run with WordPress, which makes it without question the most widely used content management system in the world. But does this mean that it is insecure due to its distribution?
Due to its popularity, WordPress presents an attractive
target for hackers. An estimated 13,000 WordPress websites are hacked daily, which extrapolated leads to an annual total of about 4.7 million hacked WordPress websites. It is estimated that about
4.3% of all WordPress websites have been hacked.
In percentage terms, just one in 25 WordPress installations is successfully hacked.
Whether you think this number is high or low - despite all these numbers, WordPress is not fundamentally insecure. It is constantly updated to close security gaps and there are a variety of security plugins that can additionally strengthen the security of a website.
That WordPress itself is rather a safe system, we also see at the people in charge of security flaws. For 99% of the security flaws in the WordPress ecosystem discovered in 2022, plugins and themes are responsible.
The main problem lies next to these plugins with security gaps rather with the users and their handling of WordPress.
On the one hand, I often see that regular updates are neglected. As a result, known security gaps in plugins, themes or WordPress can be exploited for a longer period of time.
On the other hand, the use
of unsafe or stolen passwords is added, which are responsible for 8% of the hacks on WordPress pages.
97% of attacks on WordPress are automated, often in the form of brute force attacks. In these, hackers use software to log into websites with random user names and passwords. With unsafe passwords, you make these attacks easy.
In summary, it can be said that WordPress is not fundamentally insecure despite the relatively high number of attacks. The biggest points of ingress offer security gaps in plugins and themes, if you don't promptly fix them through an update and also the use of unsafe passwords.
Does WordPress have security gaps? And if so, what can be done about it?
As you can see from the statistics above, most security problems with WordPress do not arise from gaps in the core (i.e. WordPress itself), but from outdated or unsafe plugins and themes.
Just to remind you: Depending on the source, WordPress itself is responsible for just
1-3% of all security gaps. You can see all known security gaps at any time at
WP Scan.
Remember, that regular and frequent updates are the best way to close WordPress security gaps.
However, I want to emphasize that no platform is completely immune to attacks. Therefore, it is crucial that you follow common best practices. This includes in the case of the WordPress core:
- Regular updates
- Strong passwords with special characters, random letters & numbers
- Two-factor authentication
- Automated backups
- Security checks
You will learn more about these measures in the next section.
Recommended Content-Management-Systems
On our comparison platform OMR Reviews, you can find more recommended content management systems. We present over 160 solutions that are specifically tailored to the needs of content management agencies, website operators and companies. This content management software offers comprehensive support in all aspects of website management. Take this opportunity to compare the different software solutions, drawing on authentic and verified user reviews:
Storyblok
Magnolia
Neos CMS
12 tips on what to consider when securing WordPress sites
As you may have gathered from the previous text, although there are susceptible WordPress websites, the problem is usually neglect of the website by the operator.
The following tips will help you make WordPress more secure. Don’t worry, you don’t have to implement them all!
The most important measures are the first two to three tips. If you implement them, you are very safe.
1. Regular WordPress, theme & plugin updates
Build a routine with which you regularly update your website. It is important that you keep both WordPress and your themes and plugins up to date.
I would recommend that you update at least once a week, but at least every two weeks. When updating, think about the safe sequence:
- Create a backup
- Deactivate caching
- Update plugins & themes
- Update WordPress
- Check website
Remember, that with paid plugins and themes, you sometimes do not get any information about an update in the WordPress backend. This is especially the case if you bought them on a platform like Themeforest.
2. Use secure passwords & no standard username
As many attacks take place via the WordPress login mask, a secure password is important.
You can't imagine how many people use passwords like “123456” or “asdf123”...
Ideally, do not use
real words in your password, but use a random string of letters (lower and upper case), numbers and special characters. To make it easy for you, you can have a secure password created by a
password generator.
In addition, it is recommendable to choose not “admin” or “administrator” as your username. Although this is only a small thing from the point of view of additional security, but it is also a quickly implemented thing.
The same of course applies to your hoster login, FTP accesses and e-mail accounts.
3. Set up automatic backups
Should your website get hacked, with a decent backup you can quickly and easily go back to a secure state of your website.
If your website is hosted by a special WordPress hoster, automatic backups are usually created for you. If that's the case, you don't need to install another backup system.
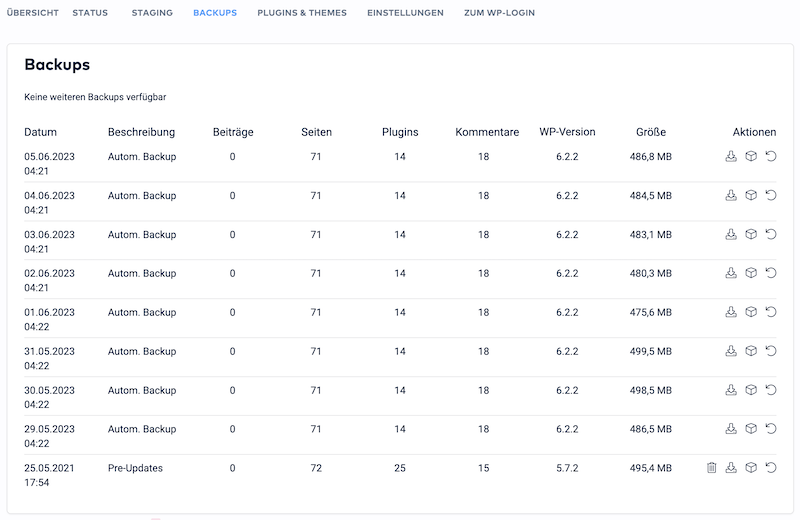
Picture: Automatic backups at raidboxes (Screenshot of the author)
However, I recommend you to download one of the backups from time to time and save it in another place (on your computer, on an external hard drive or in the cloud storage).
If you want to have the backups under control or not using a hoster where you get clean backups and smooth access to them, I recommend the free plugin
UpdraftPlus.
4. Rely on WordPress hosting
Since we have already talked about
WordPress hosting: Hosting that is designed for WordPress usually has a much safer infrastructure than a general host.
This is due, for example, to separate websites, whereby in case of successful attacks on a website, the others are not affected. In addition, important WordPress files are usually blocked by specialized hosters, so attackers have no chance here.
There are many more technical details, with which WordPress hosters can secure your website better than others. But in order not to bore you with technical talk, let's sum it up like this:
WordPress hosters have specialized their server infrastructure, software and workflows to WordPress, resulting in higher security than with general hosters.
5. Pay attention to the PHP version
WordPress is based on the scripting language PHP. This language is constantly being developed, so there are always updates here.
Currently in June 2023, WordPress requires at least version 7.4, but I would rather advise you to use 8.0.
Sometimes there are PHP security gaps, which are then closed by an update. You usually have to carry out these PHP version updates yourself with your hoster.
The good news is that it is usually done with one click, because you just have to select the desired newer version.
Complication arises unfortunately from the fact that new PHP versions occasionally cause compatibility problems with plugins and themes. WordPress itself is usually very quick to support the latest PHP versions with updates, but plugin and theme developers are not always so fast.
If you raise your PHP version and your website is no longer accessible afterwards, you can go back to the previous version. Then at least your website will work again, but of course, you should look for the cause of the error.
6. Change the WordPress admin URL
Because of the many attacks on the WordPress login mask, it can be helpful to hide or change the well-known admin URL “domain.de/wp-login.php”.
If this classic URL is not reachable, many of the automated attack programs (bots) give up directly.
A simple way to change the admin URL is the free plugin “
WPS Hide Login”. After installing the plugin, you can enter any URL for the login page in your settings, just don't forget it ;)
If you forget it, you can log in via FTP on your server and in the folder “wp-content” → “plugins” rename the folder of the WPS-Hide-Login plugin. This will deactivate it and you can log in via the standard URL.
If you already have the performance plug-in “
perfmatters” in operation, you can take the same measures without having to install another plug-in.
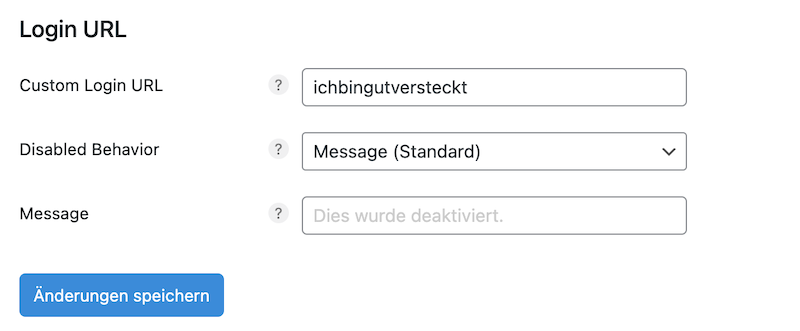
Picture (Screenshot of the author): You can change your login URL in the perfmatters plugin and thus hide it from attackers
7. Hide your used WordPress version
In general, it is good if you give attackers as few information about your WordPress website as possible. This also includes hiding the used WordPress version.
Especially older WordPress versions attract malicious bots and attackers like a bright light in the night attracts moths.
By default, WordPress shows it clearly visible to everyone in the source code:
To prevent this display in the source code, you can insert the following code into the functions.php file of your theme:
function wp_version_remove_version() {
return '';
}
add_filter('the_generator', 'wp_version_remove_version');
Ideally, you should insert this code into your child theme, as otherwise it will be overwritten with the next theme update.
8. Adjust the file permissions
With file permissions, you can control who can edit, see and run the folders and files of your WordPress installation. Therefore these permissions are a powerful tool, to prevent unwanted changes.
Here you are again with a headstart, if your website is at a WordPress host. They usually make sure that exactly the right file permissions are granted, so you don't have to do anything anymore.
Especially with general hosts,: only very general rights are granted, so you should intervene here.
The most important thing in my eyes, is to adjust the file permissions of the wp-config.php file. Important data such as the access to the used database and more lie in this file.
While very strict permissions can be given here, it makes more sense to set them in such a way that they do not hinder you in your work. You don't want to change the file permissions for every update.
For the wp-config.php fileyou should set the permissions to 640.
The .htaccess file is also very important, to which you should best assign 644.
For all other files it makes sense to give 644 or 640 file rights. I would set the folders to 755 or 750.
To change file rights, you either need an FTP access and an FTP client like FileZilla or access to the file system of your website through your hoster:
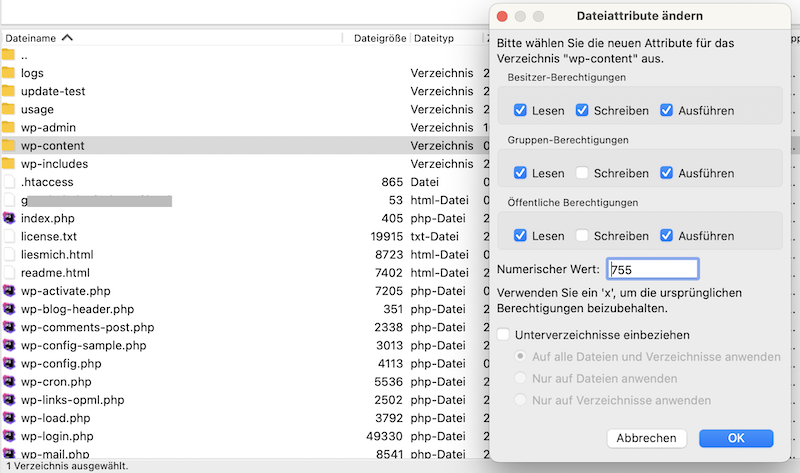
Picture (Screenshot of the author): You can change file permissions via FTP
9. Switch to HTTPS
If you have not done so yet, now it is really time!
Unfortunately, I actually see websites from time to time that still run over the HTTP protocol and thus the file transfer is not secured by an SSL certificate. Apart from the increased trust in your website, the higher speed through the HTTP/2 protocol and other advantages, HTTPS also provides more security.
In comparison to a website running over HTTP, data transferred on an SSL-encrypted page are not transmitted in plain text. So imagine you log in to your website and your password is transmitted in plain text, i.e. not encrypted. This way a hacker can easily get access to your password.
If your website runs over HTTPS, everything is encrypted and thus much safer.
The necessary SSL certificates are available for free at decent hosters via Let’s Encrypt or a similar provider.
10. Enable 2-factor authentication
You probably know them from many other providers like
Facebook,
Google and many others: the 2-factor authentication.
Just in case you have never heard of it:
Instead of only using a password to login, when “2-FA” is activated, another hurdle is set up to log in. For example, it is a code that is sent via e-mail or SMS during login and must be entered, or an app like the “2FA Authenticator” is used, with which the logging-in user has to authenticate additionally.
Major advantage is obvious: Even if someone should steal your password, the login fails at the step of the 2-factor-authentication.
To integrate the 2-FA into WordPress, you can, for example, use the free plugin “
Two Factor Authentication” which comes from the same manufacturer as the above mentioned UpdraftPlus plugin for backups.
It supports the usual apps for 2-FA and brings along useful setting options that allow you to specify, for example, whether the two-factor authentication should take place at every login, or only after a certain period of time.
11. Limit the XML-RPC interface
I know, this topic sounds very technical again, so I'll gladly explain it as simply as possible.
The XML-RPC interface was used by WordPress in the past for connecting with the WordPress mobile app or for communication with other websites to provide services like pingbacks.
Since WordPress 4.4 however, all of this has been handled by the REST API, so the XML-RPC interface is merely a remnant of the past.
From a security perspective, it is relevant because attacks can take place via the xmlrpc.php file or the connections established through it. Since we no longer need this interface since WordPress 4.4 (the version was released already in 2015), you should deactivate it.
With hosters like raidboxes or Kinsta this interface is already deactivated and also with plug-in like perfmatters, you can do this. To check whether the interface is active on your side, simply call deinedomain.de/xmlrpc.php. If you now get the message “403 forbidden” , it is already deactivated.
Use either the plug-in
Disable XML-RPC-API for this or save yourself the plug-in by inserting a code into the functions.php file of your (Child-)themes or into the .htaccess file.
If you want to go via the functions.php file, insert the following code:
add_filter( 'xmlrpc_enabled', '__return_false' );
If you want to use the .htaccess file (this only works for Apache servers, not for nginx), insert the following code:
Order Allow,Deny
Deny from all
12. Use a database prefix
The database tables, in which all your WordPress contents and settings lie, usually have the prefix “wp_”.
As already with tip six, when we hid the URL of the WordPress login, we will provide for a little more security here by changing this prefix. This makes it a little more difficult for attackers to find these tables.
During the installation of a fresh WordPress instance, you can easily change the prefix in the field provided for this purpose:
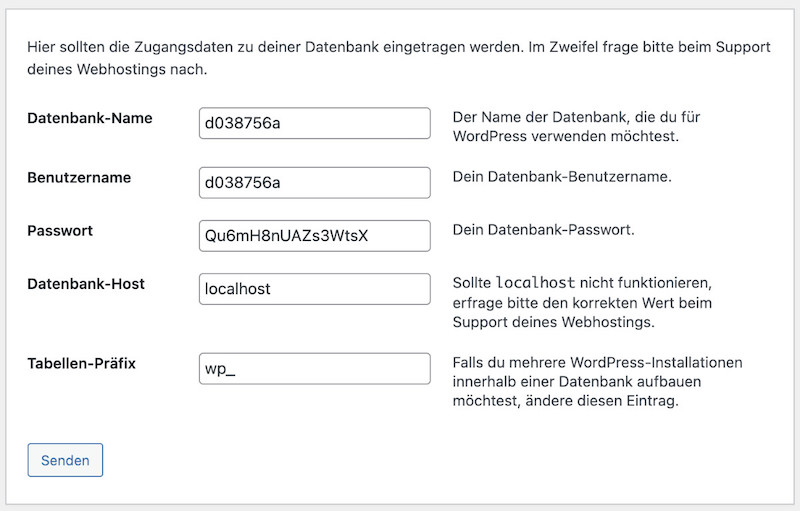
Picture (Screenshot of the author): During the WordPress installation, you can change the table prefix
Even with an existing WordPress installation
the prefix can be changed. But here caution is advised, as quite a few things can go wrong here and can crash your website.
So only do this if you know what you are doing, or let a professional do it.
If you want to check whether your website is currently infected or vulnerable, you can use various tools.
In general, all hosters have their own virus scanners running and will of course inform you if they sound the alarm. Along with my first tool tip, this is all I use myself for my websites.
When using tools to check security, please bear in mind that they are all not 100% reliable and also not all potentially indicated “weaknesses” really important and to be fixed.
- Google Search Console
The Google Search Console should be connected by every website operator to their website. If you haven't done that yet, hurry up! ;)
If Google finds out that your website has been hacked or behaves in a way that harms visitors (for example, via phishing), Google will tell you in the “Security issues” report.
- Sucuri Sitecheck
The free sitecheck from Sucuri checks your website for known malware, viruses, blacklisting, website errors, outdated software and malicious code.
In addition, Sucuri offers complete monitoring including protection of your website. As one of the probably biggest names in the WordPress security scene, Sucuri is always a good point of contact.
- WP SEC
WP Sec offers another free scanner that checks your website for malware and similar things.
If you sign up with a free account, you can let the scanner run automatically every week and receive more detailed reports.
- Pentest Tools WordPress Scanner
The also free WordPress Scanner from Pentest Website Scanner shows you security gaps in your used WordPress version, checks the website headers and checks if WP-Cron is enabled.
In the premium version, this test offers significantly more comprehensive and useful evaluations. For example, a check for security gaps within used plugins and themes and some other safety factors.
7 Plugins to Improve WordPress Security
If you want to increase your WordPress security further, you can do this with one of the many security plugins.
Here, I have two important notes for you:
For one you should only install extensive security plugins with firewalls and other technical functions if you know what you are doing. Otherwise, they can cause more problems than solutions.
Secondly you should note that most of these plugins will show you messages about unsuccessful attacks and logins (and sometimes send them via e-mail). This should not frighten you, as every WordPress website is attacked over and over again every day. So it is sadly normal.
These things are important to know, because otherwise Plugins for more security can easily backfire.
By the way: If you are with a WordPress specialised hoster, you do not need such a plugin in my view.
1. Wordfence Security
With over four million active installations,
Wordfence Security is probably the most popular security plugin for WordPress, which is certainly due among other things to the huge scope of the free version.
The plugin offers both protection against attacks, and support in identifying potential security vulnerabilities. Even in the free version, Wordfence offers a lot of useful features, among them:
- a firewall, to detect and block malicious traffic
- a scanner that checks your files for hacked code and detects changes to the WordPress core files
- Securing the login with 2-FA and CAPTCHA
- and much more...
In the premium version, the plugin is even better. Consider, that although it offers many useful features, you must also set them up correctly first.
2. iThemes Security
Directly lined up behind Wordfence Security with over a million active installations, is the
iThemes Security plugin one of the most-installed security plugins.
It has a similar functional scope as Wordfence Security:
- Protection from brute-force attacks, block all websites with iThemes Security in use for attackers
- Securing the login by 2-FA
- Monitoring changes in your files
- Easy setup wizard
In the Pro version you get many more useful features. The scope of the free version lacks some of the Wordfence features.
However, I want to emphasize that the setup wizard in iThemes Security makes it much easier for you to configure the plugin.
3. Sucuri Security
Yes right, the Sucuri Sitecheck I have already introduced to you above with the tools for checking your WordPress security. But now it’s about the plugin
Sucuri Security, which belongs to the largest security plugins with nearly a million active installations.
Like the security plugins already mentioned, Sucuri Security provides quite a comprehensive protection for your website and also offers functions for implementing many of the security tips mentioned above.
A website firewall is unfortunately only available in the paid version, but with the monitoring of changes in your files, the malware scanner and a display of potential weak points, the plugin is definitely an easy-to-set-up alternative to the two flagships.
4. WPS Hide Login
You have already read the name “
WPS Hide Login” above, when it was about securing the login page by changing the URL.
The plugin is really easy to use, as it simply adds a new field to your WordPress settings, where you can enter the desired URL for your login page. So if you are looking for a solution to hide your login page, it is the perfect plugin.
5. Disable XML-RPC
To brief you again:
With this plugin, you can disable the XML-RPC interface. It was used many years ago for functions like pingbacks or the connection to the WordPress mobile app, which is now all taken over by the REST API.
So, this function is nowadays not needed in almost all cases, but provides attackers with an attack surface.
6. WP Activity Log
If you have several users accessing WordPress on your side, it is good to understand their behaviour and changes.
WP Activity Log is ideal for this and
in a stripped-down version even free. It records what the users of your website have done, which pages or posts they have changed, whether plugins were installed and much more. This way you can identify suspicious behaviour early on.
7. UpdraftPlus
As you read at the beginning of this guide, one of my top 3 tips for more WordPress security is the automatic creation of WordPress backups.
With
UpdraftPlus automated backups are set up within a few minutes. The simple handling of the plugin makes it a super choice even for beginners.
Conclusion: WordPress can be easily secured with simple measures
Well, what should you take with you from this detailed guide?
First of all, that WordPress is not an insecure system. Most successful attacks take place via plugins and themes, and the user also plays a crucial role in that a large part of the hacks can be prevented by regular updates of WordPress, plugins and themes.
There are many methods with which you can make WordPress even safer. The most efficient of them are probably the use of a decent WordPress hoster, regular updates, safe passwords and automated backups.
Implement these measures and your website will be very safe. If you want, you can of course also implement some more from the mentioned tips, good luck!




